Geo-temporal Characterization of Security Threats
Overview | People | Collaborators | Sponsors | Publications | Tools
In some countries, computers encounter disproportionate quantities of cyber attacks, while in other countries computers host disproportionate quantities of these attacks. Empirically identifying factors behind such phenomenon can provide a sound basis for policies to reduce attack encounters and hosting. In previous work, however, identifying these factors is mainly based on expert opinions, not statistical evidence.
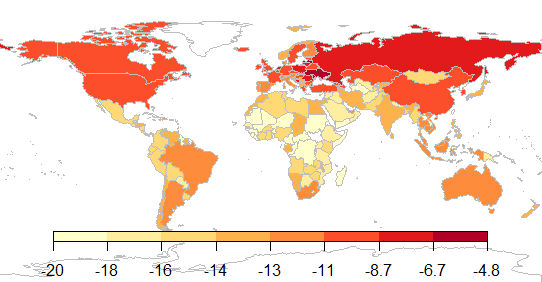
Hosting of web attacks: average number of web attacks launched per computer (log scale)
In this project, we built statistical models that explain the international variation in the number of attacks encountered and hosted. I used the Symantec Intrusion Prevention System (IPS) telemetry data and Symantec Anti-Virus (AV) telemetry data both collected from more than 10 million Symantec customer computers worldwide, and combined that data with an attack description database that we built based on Symantec online attack descriptions. The IPS data mainly cover network based attacks (web attacks, fake applications, and exploits), while the AV data mainly cover malware(trojans, viruses, and worms).
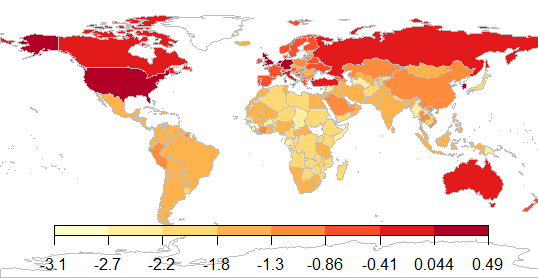
Exposure to web attacks: average number of web attacks encountered per computer (log scale)
We used regression analysis to estimate the effect of countries wealth, cyber security research and institutions, corruption, web usage, and international relations on the number of attacks encountered and hosted. Our work has shown that Sub-Saharan Africa is the most exposed region to malware because of widespread computer piracy in that region. Our research has also shown that Western European and North American countries encounter disproportionate quantities of network based attacks because these countries are rich, thus attacks on these countries are very lucrative. Finally, we found that the combination of widespread corruption and reasonable computing resources in Eastern Europe creates a favorable environment for hosting cyber criminal infrastructure.
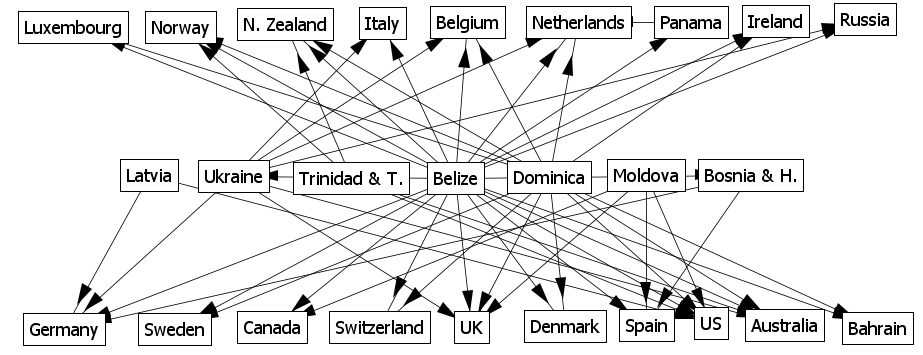
Country to country web attack network (only strongest links are shown)
This work indicates that reducing attack exposure and hosting in the most affected countries requires addressing socio-technical aspects that are not traditionally considered cyber security problems. For example, making the environment in Eastern Europe less favorable to hosting cyber crime infrastructure requires a focus on cracking down on corruption. Other interventions such as providing cyber security training and increasing cyber crime penalties are unlikely to be effective and may even be counter productive; often, when corruption is widespread, increasing penalties may increase the crime rate.